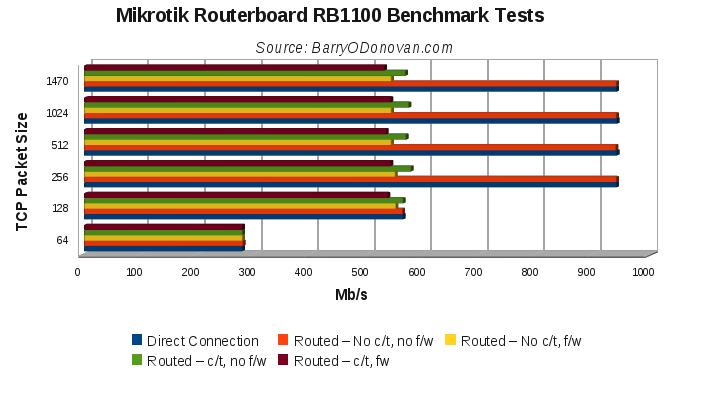
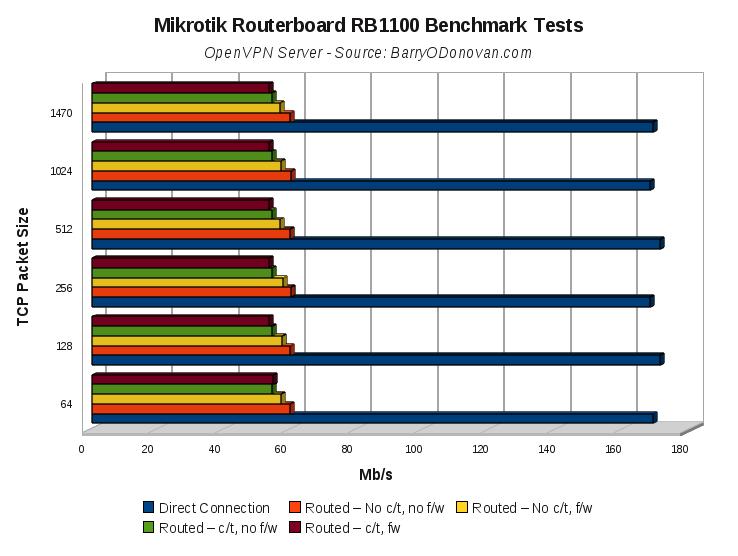
Continuing on from today’s earlier post, Benchmarking the Mikrotik Routerboard RB1100, I now present some results for the RB750 and RB750G using the same methodology and platform.
The RB750 and the RB750G are two identical looking routers intended for the SOHO environment:

The specifications for the RB750 (with differences for the RB750G in italics and parenthesis) are:
- five FastEthernet 100Mbps (Gigabit 1Gbps) ports;
- 32MB DDR SDRAM ;
- 64MB on board NAND storage;
- Atheros AR7240 400MHz (AR7161 680MHz) CPU;
- powered by PoE or power jack;
- up to 3W (6W) power consumption;
- ports 2-5 share dedicated switch chip allowing full 100Mbps (1Gbps) throughput;
- all ports can be individually configured.
- €31.73 (€54.61) from Wireless Connect.
Both routers come with an L4 license of Mikritik’s RouterOS which is built on the Linux kernel so anyone familiar with Linux networking will get up to speed on these boxes in no time.
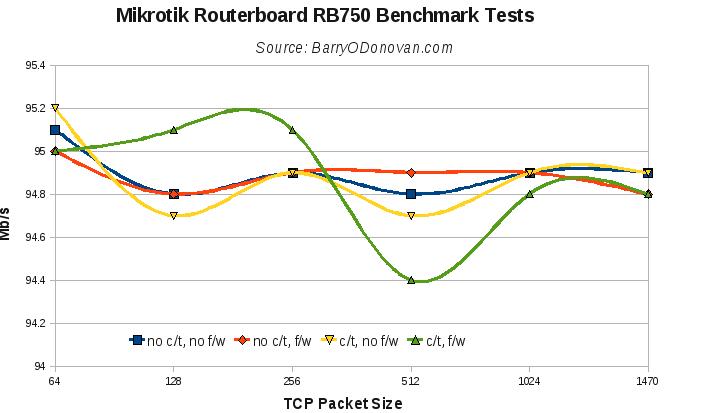
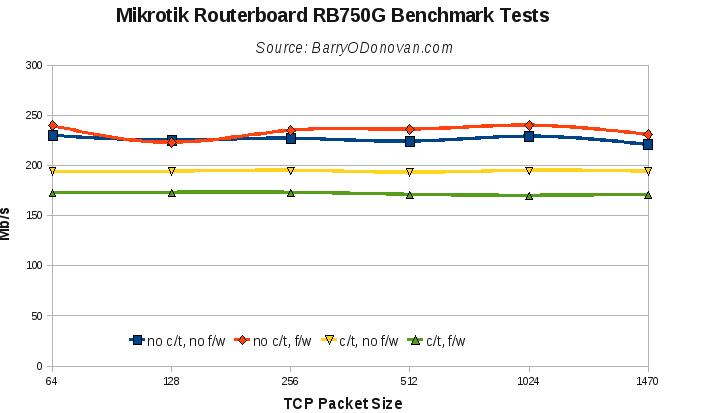
As a disclaimer in case it is not clear, all routing tests are done using just two ports – one for the traffic generator and one for the receiver – with the device under testing routing the packets between two networks. As such, on the RB750, the maximum throughput we could achieve would be 100Mbps.
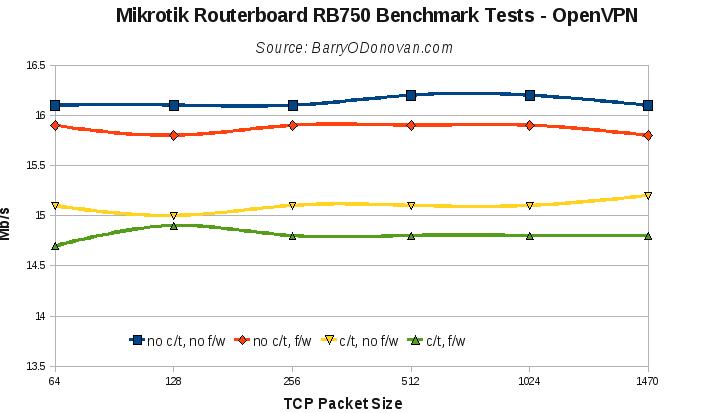
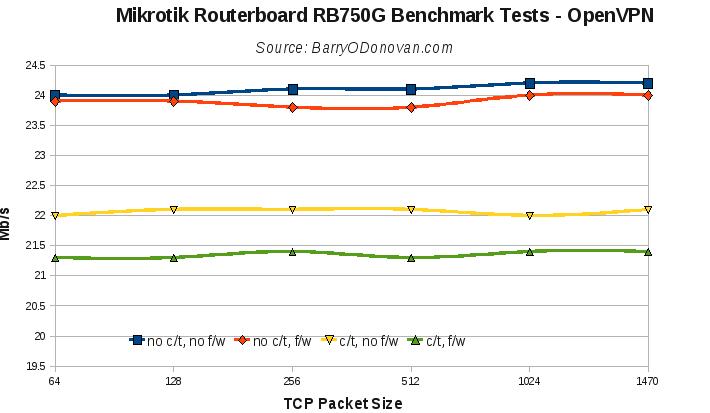
I ran tests for plain routing and also, in evaluating it for certain uses, over a VPN tunnel.
All results are presented below. Given the wealth of features, I think these are super boxes at a super price. So far I’ve put them on the end of an Imagine DSL line providing IPv4 and v6 over PPPoE and the end of a 30Mb UPC line taking its UPC IP via DHCP. They provide firewall, NAT, port forwarding, OpenVPN tunnels, QoS, DHCP, DNS caching and VLANs for phone / VoIP and managment networks.